Early Identification: Key to Effective Risk Management

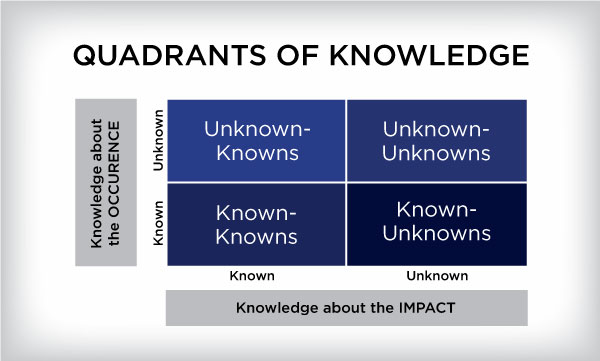
Risk practitioners tend to categorize risks based on the level of knowledge about the occurrence (known or unknown) and the level of knowledge about the impact (known or unknown).[1] Known risks can be prioritized by level of impact and likelihood of occurrence and a plan forms accordingly.
The Deepwater Horizon oil spill is a classic example of a major catastrophic event that many believed was caused by unknown risks, also referred to as unidentified risks, rearing their ugly heads.[2]
Early identification is every risk manager’s aim. Taking risks out of the unknown into the known allows them to be more effectively managed.
Risk Assessments Help Identify Risks Sooner
“The absence of evidence is not evidence of absence, or vice versa.” – Donald Rumsfeld
A formal risk assessment process can help your organization pull risks out of the unknown, into the known. Often unknown or unknowns aren’t truly unimaginable, they are simply being ignored for some reason or the people or person who knows of the risk hasn’t brought it forward. A risk assessment process can help draw them out.
Consider the risk of active assailant incidents that are quickly hitting the awareness of managers in just about every facet of society. In the past, while the risk may have been known to some and the impact known to be extremely severe, the likelihood was considered low, and therefore was not always prioritized. Today, the rising incidence of active assailant situations across locational categories, puts them unmistakably in the known risks category and leaves no room for organizations to be without a risk management plan. Over 80 percent of these incidents occur in the workplace.[3]
A formal risk assessment process looks like this:
- Identify emergent and existing threats targeting your industry and your organization
- Determine internal and external sources of threats and be able to assign mitigation measures
- Evaluate the likelihood and outcomes of each risk event; prioritize accordingly
- Recommend proper security and mitigators to address your specific threats
- Check for suitability and employee compliance; check for effectiveness
- Evaluate, monitor, observe, and assess new or evolving threats, and optimize accordingly
Identifying your risks early and often can help protect your people, your brand, and your profits. Are you clear on where your organization’s vulnerabilities lie? Are you aware of emergent threats and how they might impact your business? If your risk assessment process needs to be revitalized, we invite you to request a meeting with a Lowers & Associates professional.
[1] https://www.pmi.org/learning/library/characterizing-unknown-unknowns-6077
[2] http://www.tandfonline.com/doi/abs/10.1080/13669877.2014.983949?scroll=top&needAccess=true&journalCode=rjrr20
[3] https://www.shrm.org/resourcesandtools/hr-topics/risk-management/pages/fbi-active-shooter-work.aspx
ABOUT THE AUTHOR